A recent controversy has emerged around Espressif’s ESP32 microcontroller, following the discovery of undocumented Bluetooth HCI commands by security researchers at Tarlogic Security. Initially described as a "backdoor," this characterisation sparked significant debate and was later revised to acknowledge these commands as debugging features rather than a deliberate security vulnerability. The initial media coverage painted a picture of a serious security flaw, only for later clarifications to tone down the exaggerated claims.
The issue was reported during Tarlogic’s presentation at RootedCON in Madrid, where researchers detailed the existence of 29 undocumented vendor-specific commands in the ESP32's Bluetooth stack. These commands allow memory manipulation, MAC address spoofing, and packet injection, all of which could, in theory, be exploited under certain conditions. The researchers suggested that these capabilities could allow attackers to gain persistence on compromised ESP32-based devices, manipulate Bluetooth communications, or launch attacks against other nearby devices. Tarlogic’s findings were part of their efforts to promote their new USB Bluetooth investigation tool, designed to provide raw access to Bluetooth traffic for security research. By using the ESP32 as a test subject, they identified these undocumented commands, which Espressif had not publicly disclosed. While their research is technically sound, the way it was presented raises questions about whether it was exaggerated to draw attention to their product. It is common for security firms to highlight vulnerabilities in widely used hardware as a way to market their capabilities, and ESP32’s immense popularity made it an attractive target for such a narrative.
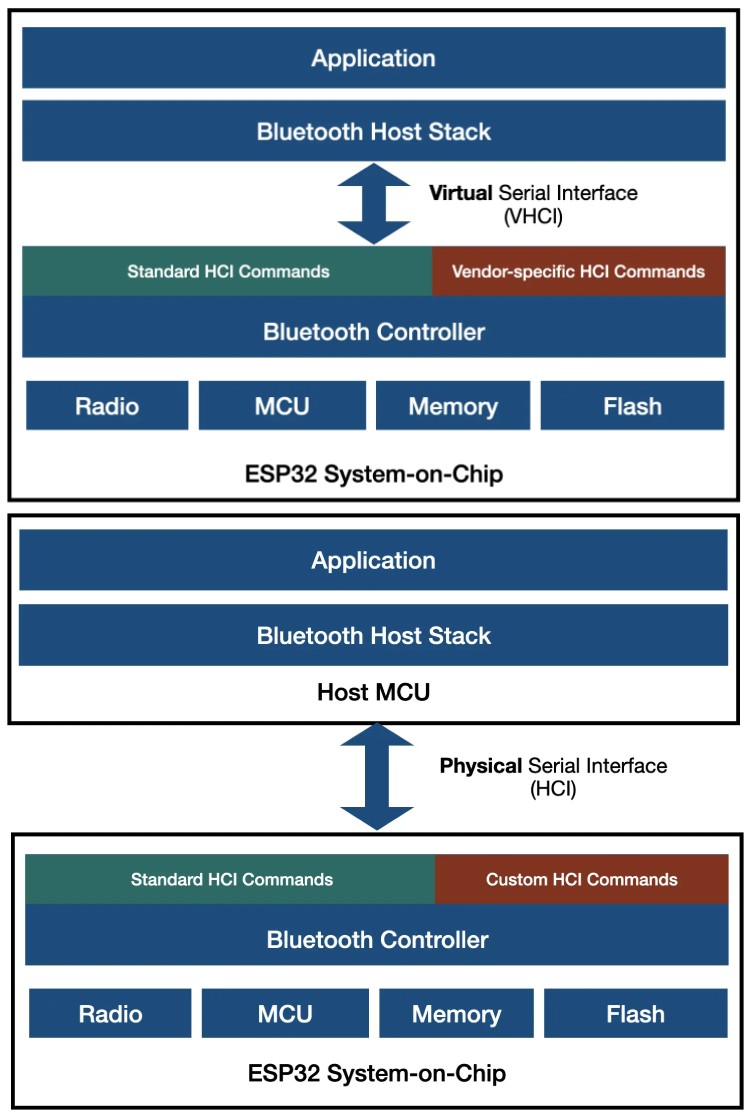
Espressif responded to the claims, clarifying that these undocumented commands are internal debugging tools that do not pose an inherent security risk. They stated that these HCI commands are used for internal testing and debugging during development and manufacturing, a common practice in embedded systems. The company emphasized that these commands are not remotely accessible via Bluetooth or network access and can only be executed from within the ESP32 firmware itself. If an attacker already has such access, they would already have complete control over the device, making these commands redundant as an attack vector. Espressif also confirmed that only the original ESP32 series contains these commands, while newer models such as ESP32-C, ESP32-S, and ESP32-H are unaffected.
Such Undocumented vendor-specific commands are common across various semiconductor manufacturers, as they are routinely included in microcontrollers and other chips for internal testing, debugging, and hardware validation during development and production. These commands are generally restricted to development and manufacturing environments and are not intended for end users. The issue has been assigned CVE-2025-27840, with both NIST and MITRE giving it a severity rating of 6.8 (Medium). While this rating indicates some level of concern, it does not imply a critical or widespread security threat. Exploiting these commands would require either physical access to the device’s USB or UART interface or full control over its firmware. In a less common scenario where an ESP32 acts as a Bluetooth co-processor for an external host, an attacker could issue these commands if they had already compromised the host system. However, in such cases, the security risk lies with the host rather than the ESP32 itself. To address any lingering concerns, Espressif announced that they would release a firmware update disabling these undocumented commands.

