Security

|
Mouser Brings Intelligence from the Cloud with Edge Computing Online Resource Hub for Engineers February 10, 2026 – Mouser Electronics, Inc., the industry's leading New Product Introduction (NPI) distributor with the widest selection of… |

|
Infineon launches the next-generation of USB 2.0 peripheral controller with the EZ-USB™ FX2G3 Munich, Germany – 20 January 2026 – Infineon Technologies AG (FSE: IFX / OTCQX: IFNNY) is introducing the EZ-USB™ FX2G3, a next-generation USB 2.0… |

|
STMicroelectronics Brings First Matter NFC Chip for Simplified Smart-Home Device Onboarding STMicroelectronics has introduced a Matter NFC chip, which is a first for the sector. With just a tap, the new ST25DA-C chip allows users to add… |

|
HackStar, A USB Ethical Hacking Tool Capable of HID Emulation Remotely Creator Hathey Mash has launched a Kickstarter campaign for HackStar, described as an advanced ethical hacking tool. It is capable of acting like… |

|
Nuvoton Launches 4th Generation Gerda HMI Display ICs for Automotive Safety and UX Nuvoton Technology Corporation Japan (NTCJ) has started mass production of its 4th-generation Gerda HMI display ICs, available in three variants.… |

|
Renesas Launches DA14533: Auto-Grade Bluetooth LE SoC for Low-Power Wireless Connectivity Renesas Electronics has introduced the DA14533, its automotive-grade Bluetooth Low Energy (LE) SoC, designed for tire… |

|
Espressif Shuts Down “Backdoor” Hysteria: ESP32 Debugging Feature Misrepresented as Security Threat A recent controversy has emerged around Espressif’s ESP32 microcontroller, following the discovery of undocumented Bluetooth HCI commands by… |

|
Indian Army Develops Cost-Effective KHARGA Kamikaze Drone The Indian Army has developed the KHARGA Kamikaze Drone, a cost-effective and efficient aerial system designed to meet… |
|
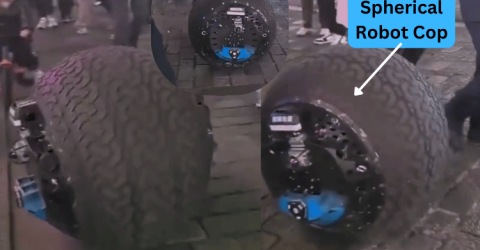
RT-G: AI Based Spherical Robot Cop to Maintain Law and Order in Chinese Streets Ever wondered what it would be like if a spherical robot patrolled our neighborhood to maintain law and order? It… |
| |
Silicon Labs SiWx917Y Module: Compact, Pre-Certified Module with Enhanced Security and Ultra-Low Power IoT Connectivity Silicon Labs has introduced the SiWx917Y, an ultra-low-power module designed for secure and efficient wireless connectivity, integrating Wi-Fi 6… |

