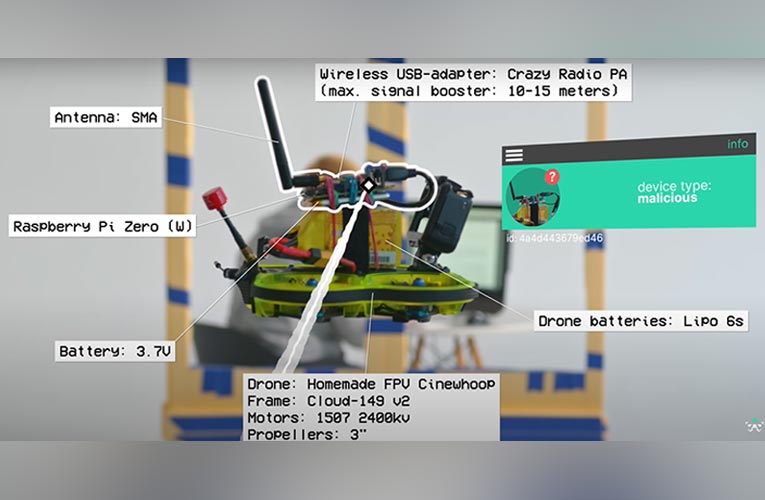
In an era where technological advancements seemingly know no bounds, a new breed of cyber threats has emerged, utilizing the power of invisible drones and the sneaky technique known as Mouse Jack. These covert infiltrators pose a grave risk to computer security, breaching systems with lightning speed and precision. The drones, capable of maneuvering where humans cannot, silently fly through fortified perimeters, entering buildings through open windows, and wreaking havoc on computer networks. With the aid of the Mouse Jack vulnerability, hackers can exploit wireless adapters found in numerous devices, using forged signals to gain unauthorized access to computers within a matter of seconds.
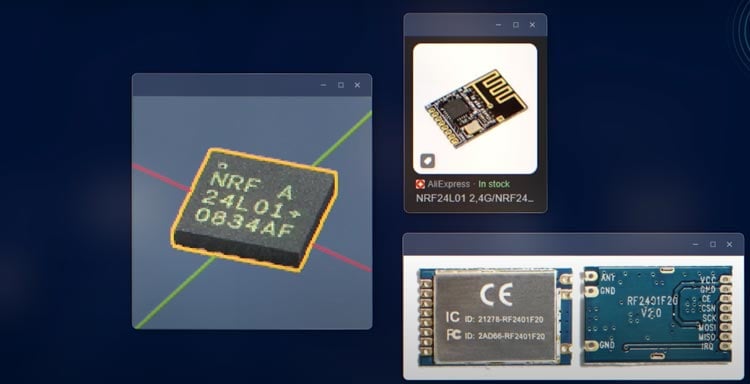
The use of drones in hacking operations provides a distinct advantage over traditional methods. Their small size and agility enable them to bypass physical barriers and swiftly navigate to targeted areas, often going unnoticed. By leveraging zero-click attacks like Mouse Jack, these drones execute their mission seamlessly without interrupting their flight. This technique targets the wireless adapters of widely-used devices such as mice and keyboards, taking advantage of the unsafe wireless radio interface of the NRF 24L chip. Unbeknownst to many users, this vulnerability allows hackers to forge signals, imitating legitimate devices and granting them undetectable access to their victims' computers.
To combat this rising threat landscape, the importance of robust anti-fraud solutions cannot be overstated. Companies like Samsung have recognized the exponential growth in cybercriminals' capabilities and sophistication, developing comprehensive compliance solutions to protect businesses and their reputations. These solutions combine various cutting-edge technologies, including transaction monitoring, email and phone verification, anti-fraud systems, and pixel analysis. By investing in these proactive measures, individuals and organizations can fortify their defenses against unseen threats, securing their digital lives in an increasingly interconnected world. It is imperative that we remain vigilant and embrace advancements responsibly, while actively safeguarding ourselves against the shadowy dangers that lurk within our interconnected devices. Here’s the complete video which explains it in brief.

