
Today Human civilization is highly dependent on computers and other machines. Everything around us from a simple alarm clock, to a complicated online banking system, works based on the program written for it. But how dependable are these programs, it is okay to wake up late when your alarm clock fails you, but think about losing your life’s savings just because your banking system was compromised. In fact, an article from Forbes states that in 2017 banks have lost about $16.8 billion to cybercriminals. This puts a big frown on our face, if these programs are subjected to loopholes, How can we trust them to drive our future autonomous cars? How can we trust them to automatically administer drugs and help take critical decisions in biomedical field?
Behold! The power of Blockchain
Well! The solution for it is already here and it is called as “Blockchain”. Blockchain is a way to build this trust by coding it as a computer program. The idea is not new and has an already been proven with Bitcoin. For those who are new, Bitcoin is a computer programmed crypto currency, it is a type of electronic cash with no centrally administrated system, no central financial branch or headquarter under any country, it’s a self-maintained network. Bitcoin was the brainchild of a person or a group of people with an anonymous name “Satoshi Nakamoto” who laid the foundation of it by authoring the paper Bitcoin: A Peer-to-Peer Electronic Cash System.
As Adam Draper, CEO of Boost VC once stated “The Blockchain does one thing; it replaces third-party trust with mathematical proof that something happened.” The whole purpose of this thing was to prevent a trusted third party from getting a share for the transactions made between a buyer and seller. Here a trusted third party such as Visa, MasterCard etc, takes a small amount of fees on every transaction and we allow this for the trust factor which is being created by the human touch behind it. And through the codification of trust with the help of bitcoin these transactions are all safe without relying on any trusted third party.
The technology behind Bitcoin which makes it so secure is Blockchain. Though the initial implementation of the Blockchain was done on making secure payments without any role of third party, today the architecture of the Blockchain is now being used in many applications like security, Internet of Things (IoT), smart contracts, smart appliances, supply chain and etc. In this article we will learn more about Bitcoin and it potential to make significant changes to technology as we know today.
What is Blockchain and how does it work?
If something is already available in the public, how it can be stolen? This is the first principle of Blockchain system. Decentralization, there’s no central authority governing over the system and it has a distributed ledger system. Since all the data is available online, anyone on the internet would be able to see the records stored, which makes the whole system transparent. It would be like spreadsheet which is distributed among different users and in turn is updated in everyone’s system when the spreadsheet is being used. So the data stored in the spreadsheet is not held by a single centralized server but is kept in public hosted by millions of computers, accessible to anyone on the internet. So there’s no centralized system for a hacker to corrupt.
Blockchain provides all of its users a maskable identity. One identity is present in public but at the same time other is hidden from all. Well that’s the second principle of Blockchain and according to which some people says Blockchain provides transparency while the others say it provides privacy. The person’s identity is hidden under cryptographic code and the only available identity is the cryptographic public address. So that means person is present in public and all of its transaction are available but all under a cryptographic code name.
So instead of seeing kanika sent 1 BTC (Bitcoin), you would see something like
1MF1bhsFLkBzzz9vpFYEmvwT2TbyCt7NZJ sent 1 BTC
Here’s a transaction data of 1MF1bhsFLkBzzz9vpFYEmvwT2TbyCt7NZJ person
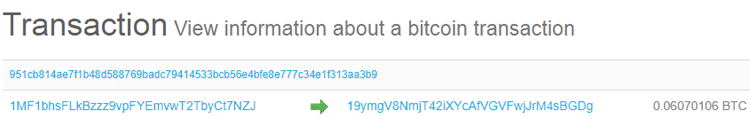
The third principle of the Blockchain is that one cannot just write off the books to save him/them from the embezzlement or laundering the money. In real world where people just change or edit the details of the documents to save themselves is not possible in Blockchain. Here it is intelligently prevented and that’s also the reason for why Blockchain is named as Blockchain.
SHA256 Hashing Technique
To understand how this is done, we have to first understand the principles of cryptographic hash function. In layman term hashing means taking a string (or a sentence or a paragraph in simple words) of any length and converting it into fixed length string. An important difference between hashing and encryption is that encryption can be reversed i.e. decrypted but hashing can’t be reversed or is very hard to revere as compared to decryption.
Bitcoin and other crypto currencies, generally use SHA-256 hashing algorithm, which gives an output of fixed length. Now let’s see how hashing works by taking an implementation of SHA-256 algorithm using SHA 256 calculator. Firstly, we input circuit digest into the data field of calculator and see what is the output in the form of SHA 256 hash.

So the conversion into SHA 256 gives a 256-bit (32-byte) code which is unique. If we input the text “circuit digest” we get the output as
394c19455b15b23783bd52228a698695d9454c806d983ae7bfe3bd80d32e1ac7
Now if we change the input a little say we make the first letter capital, whole of the code will change, even one can’t even detect the minute change through the code.

Now, the cryptographic code for Circuit digest has changed into
e06ed37daa54ca41c6a2ee656c50a703d85fae76f0954534ec137983f6f37062
SHA – 256 can convert any string no matter how long it is, into 256-bit character length. This factor becomes really important when one is dealing with large amount of data and transaction, so instead of remembering the full length data one has to only remember the fixed length hash.
There are several properties of SHA – 256 hash which makes it ideal for cryptographic hash one of them is Avalanche Effect, which states that even a small change in the input will bring out a large change in the output. The same is illustrated above. One can clearly how different the hash code is different for circuit digest and Circuit digest, which only differ in a single case letter.
Now for understanding how cryptographic hash works in Blockchain, one has to understand the data structure behind the block chain. Blockchain works on linked list data structure, which contains the data and hash pointer which significantly points to the previous block, now the hash pointer is not different from a simple pointer, but instead of containing the address of the previous block it contains the hash code of the data of the previous block.
This small change in the pointer makes the Blockchain so amazing and immutable. If someone tries to change the data in the 4th block, then it would lead to change the hash pointer of 3rd block and then eventually the second block and will continue further and to change the whole chain so practically it is impossible because of the decentralized structure of it. These three principles give Blockchain the immutability and strength that it can be used in vast application space from security to management.
How Blockchain can drive the IoT Ecosystem more securely
The most amazing thing about the Blockchain is its architecture. Maintained by a peer to peer network, where the entire workload is entirely distributed among all the peers that are equally privileged. This peer to peer network removes the need of the central server, all the data is handled by the peers or nodes of the network. On the other side the centralized structure of IoT creates a problem, where a million of devices of the scale of citywide network are expected to be leveraged for entering into a system. A single malicious device in the IoT network can take down the whole structure and not only IoT network but also other network which are in relation with the central server of the devices.
While the studies show that there is a fortune in both the markets, the global IoT market is expected to grow by 475 Billion by 2020 and for the Blockchain Gartner has predicted that it would add $176 billion in business value by 2025, and $3.1 trillion by 2030. However, the existing problem which is in the way for the late adoption of IoT tech is its security. Blockchain and IoT together could solve the problem of IoT Security Challenges and can exhibit a better synergy.
The international patent filing trend is also predicting the same story, the analytic study from Google patents which involves 126 unique patents focusing purely on the IoT and Blockchain which are filed between the years 2016-2019. Some of the ways were the distributed architecture of the Blockchain could be really helpful in improving the security patches of IoT network.
- The distributed ledger architecture of Blockchain could really help in tracking the values from the sensors without a need of a central sever.
- Cloning of nodes with malicious nodes could be prevented easily.
- Need of third party platforms for trustful distribution of data could be eliminated, as IoT sensor can exchange data through Blockchain.
- Autonomusity could be brought in IoT devices with the implementation of the smart contracts.
- A single device failure would not affect the whole architecture if the whole system is implemented with Blockchain’s Peer to peer network.
- Intermediary costs could be eliminated with the help of Blockchain architecture.
How companies are implementing Blockchain and IoT together
Smart devices in our homes like Amazon Echo or Google dot slowly has started to play a vital role and has access to critical information. The centralized approach to exchange data generated by the IoT devices lacks owner’s privacy and security.
Let’s look into the case study of an innovative solution developed by TELSTRA, A communication and media company in Australia. The company has implemented Biometric security with the help of Blockchain to make sure that no one can alter the data from the smart devices. User’s sensitive data which can provide access to smart home and various smart devices such as Biometrics, voice recognition and facial recognition is stored on the Blockchain. Once the data is saved on Blockchain it can’t be modified and access can be provided to the right person, no trespasser can modify it and crack into it.
Role of Blockchain in other sectors
Blockchain gives it users a trust factor in the form of code, it gives a value and authenticated digital information, which shapes various applications around it including the most significant in financial asset management.
File Storage
Blockchain being a decentralized system can really help in storage system, a great example of it is Torrent, torrent moves around files in a decentralized way solely depending upon the peer to peer network instead of relying upon the client server architecture. Similarly, the files could be stored in the Blockchain and for some sensitive files a public-private Blockchain could be used to store the data and making it accessible to the user when a private key in inputted to it.
Data Management
General Data Protection Regulation (GDPR) policy in European legislation gives the owner of the data more control over it rather than the companies. Blockchain could be really useful in implementing it, with the use of public-private Blockchain, which gives the user a freedom to manage his data and further he can monetize over it, there are many companies which are collecting the user’s gene data and further can sale it to various companies with the permission of the user and by paying them in the form of crypto currency.
Polling
One of the ability of Blockchain is to convert the known user identities into cryptographic form; it could help to run transparent government and polling operations wherein all the votes of each individual could be released in public but under a cryptographic name. It could help in clean elections without any chance of corruption.
Sharing Economy
The new upcoming economy trend is one, in which most of the assets are not owned by anyone, but used by everyone on a sharing basis. Moreover, the sharing economy is based on the consumer trust, top rated products, cars, drivers are the one which are rewarded by the system and the one factor based on which consumer chooses from.
Global companies like Uber and Airbnb rely upon sharing economy for the business in which people are willing to lend their assets in a wide pool of market to get access to more and more customers and same is with their Indian counterparts Ola and OYO. Transactions between the customers and platforms can be made more transparent and accessible without the review of third party by using the peer to peer system of the Blockchain. Moreover, Blockchain is being a potential threat to companies like Uber and Airbnb where whole of the system can be relied upon the Blockchain, this article on medium would give you an insight to it.
Intellectual Property
Redistribution and illegal use of creative works is a serious problem to the owner of the copyrights. The illegal use of creative works affects the market image of the owner, and most time the plagiarized content is in digital form and is available on the internet easily. Blockchain could be a smart solution to it for preventing the illegal and improper use of intellectual property assets such as copyrights.
Blockchain and Artificial Intelligence together can be used to find the illegal use cases of your work on the internet and accordingly you can legalize your ownership over it if your work is priorly available on the Blockchain. Many companies are using Blockchain in the field of IP asset management, here is the article from Forbes magazine which would give you more insight to this field.
KYC and Other Verifications
Banking and other financial institutes are currently moving towards the Know Your Customer procedure for the verification process, although this process is labor intensive and cumbersome for every new customer and for every new institute with which the customer or institute engages. Blockchain can provide solution to it, which will not only reduce the costs but at the same time would increase monitoring and analysis. It could be done by bringing the whole verification platform on Blockchain and performing the cross-institution client verification which will facilitate by real-time data exchange between intra- and inter- institute verification system.
Smart Contracts

A smart contract is a digital document intended to verify, facilitate or enforce a negotiation or the statement held by a contract. The difference between a traditional contract and a smart contract is that smart contracts are withheld and enforceable without third party interference.
It helps to exchange property, shares, money etc. in a transparent and a conflict-free way while avoiding the services of third parties such as court or a notary. A simple example of it is when someone lends a house to a person then that person pays by crypto currency to the system and generates a digital contract. When the owner of the house lends you the digital Key of the apartment which is valid for the date mentioned on the contract, not before that, and when your lease is over you can regenerate it by paying the system, otherwise your key would be held invalid.
Since its advent Blockchain has seen a huge increase in attention and is evolving into different technological sectors. For its further development we have still wait to know what future holds for it.





