
IoT devices have now turned to be an essential part of our daily lives, which is also transforming our cities, officies, and entire house into a smart habitat. According to researchers, in the coming few years, all the devices will be connected to each other and to accomplish this task, the electronic items require to be extremely smart and secure. Hackers are targeting IoT devices massively on a daily basis and hence, any company utilising or making an IoT device has to focus and prioritize on top-notch security.
Chips are the most worried aspect because it is now the backbone of every electrical and electronic goods. According to a report of international research and intelligence firm IoT Analytics, in the last 26 years around 100 billion ARM-based chips were shipped, but now the growth has exceeded to such an extent that in the last four years, another 100 billion ARM-based chipset were shipped globally. By the end of 2021, there will be 12.3 billion connected devices and towards the end of 2025, the volume will exceed 25 billion. With the escalation of connected devices more chipsets are deployed in the market and they are not at all secured from a hardware perspective. The more vulnerabilities in the market, the more unsecured will be your deployments, systems, and solutions. Satyajit Sinha - Senior Analyst - IoT Analytics told CircuitDigest, “It is very imperative to secure the IoT ecosystem. Traditionally, securities are only software securities or firewalls, but IT demands a robust security. The systems will generate much more data and more devices will be connected and so, securing just one system will not solve the painpoint. Nonetheless, we need to take the approach of four layers of security, hardware, software, network, and cloud.”

The Latest and Current Layers of Security for IoT Devices
If you are deploying a new solution, then it is preferable to deploy an embedded solution, which is embedded within the secured MCU or SoC. The point to be noted is that there is already an existing solution, but an embedded solution cannot be implemented on top of that and hence, Hardware Security Module (HSM) always makes sense and it will provide an equal amount of security. Then, the software security can be implemented on top of a secured MCU embedded like an Azure-based device. The basic level is network security, which is the implementation of AI and machine learning at the network core. This implementation tracks and creates the data aberration. Cloud security is also an integral part of hardware security as well.
The pillar of hardware security enables the “hardware root of trust” that utilises asymmetric encryption. A hardware root of trust is the platform on which all secure operations of a computer system rely. It contains the keys used for cryptographic functions and enables a secure boot process and on the other hand, a secure tunnel is also crafted for the secure flow of data from chip to the cloud, ensuring data security at rest and in transit.
There is a tamper-resistant secure platform, known as Secure Element (SE) that has the potential of hosting various applications in a very secured way and also their cryptographic and classified data following the security necessities and rules established by the verified authorities. Another uniqueness of SE is that it can be utilized in numerous form factors (UICC(SIM), embedded secure element, and micro-SD) and multi-application environments.
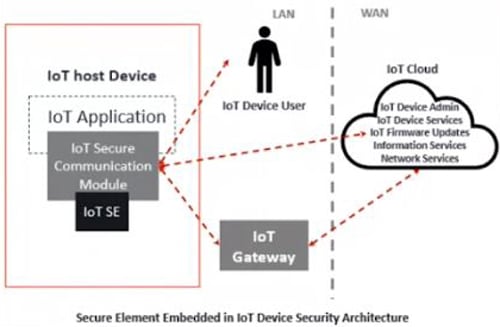
Source- IoT Analytics
The artifacts utilised to validate a device can be securely stored by a Trusted Platform Module (TPM) and that artifacts consist of encryption keys, passwords, or certificates. The uniqueness is that TPM is independent when compared to all other platform components such as OS, processor, and memory. It uses a root key protected in silicon to enhance native operating system file and folder encryptions and lays the foundation for authentication of TPM-enabled devices. TPM is one of the oldest developed securities. We have seen the deployment of TPM in PCs, laptops, even Google implemented it on their smartphones as well. “One of the key changes to the TPM was the titan chip when it was implemented by Google India in their servers. It changed the perspective of the market that security is not just limited to the devices, it’s also in centers and servers that need to be secured from the hardware perspective,” added Sinha.
Why Chip-to-Cloud is Important to Secure IoT Devices
According to various media reports, a year back during the COVID-19 pandemic, Alibaba declared to counter the augmenting demand for software business with an investment of over $28 billion in cloud architecture. Be it off-site or onsite, connected or IoT devices have turned out to be important to transforming enterprises swiftly. For the enhancement of connectivity technologies, the implementation of enterprise computing based on cloud plays an imperative part. There is a saying that ‘you cannot have profit before you have security.’ Hence, cutting-edge connectivity between the devices is the urgent need of the hour that can be revoked by cyber-threats.
Source: IoT Analytics
The point is how Chip-to-cloud will transform or revolutinse IoT in the coming years. It is required to look for a trusted hardware-the processor before making a smart device. The processor or the chip must offer state-of-the-art security measures such as a secure RAM, a hardware random number generator, and a cryptographic accelerator. Now, when it gets related to connected devices, reliable software architecture is required because it discards hackers from infecting and cloning our gadgets. Then, a secure connection to the cloud turns supreme and the next step is the impeccable management and supervision of our device. Chip-to-cloud is a unique technology that helps craft secure-by-design devices utilising microchips that are energy-efficient because it will further help stay connected to the cloud every time.
Corporate giants such as Amazon and Microsoft are closely working on the implementation of this solution for a quite a long time to help users from being hacked. To stay protected against cyber-threats the development of processor-based security solutions is important. The Pluton processor was unleashed by Microsoft sometime back and the Chip-to-cloud security is already deployed in Microsoft Xbox and Azure, but deployment of this technology on a rapid scale needs to be done.
Microsoft Azure is one of the keys for secure chip to cloud. The Azure sphere in the cloud thus embeds with a private key that enables asymmetric encryption and authenticates devices with paired public keys at the time of manufacturing.
For instance, in North America, international coffee chain Starbucks has deployed Microsoft Azure in all its chains. Each of the outlets have more than twelve pieces of equipment that works for more than seventeen hours a day and are required to be connected to the cloud for data related to beverages, any speculative maintenance to fight shy of disruptions, and asset monitoring. It embeds public secure keys within a secure MCU/MPU backed by its Pluton security subsystems.
How to Secure IoT Devices in Post-Quantum World
The development of quantum computing would jeopardize the most popular public-key encryption systems even though it is still in the early stages of development. These encryption systems are now essential to secure the internet because they are equipped with the potential to tackle and offer top-notch security in various communications platforms that are not security proof. With the increasing demand, it is now extremely challenging to offer state-of-the-art security to the IoT enabled devices because most of them are dependent on batteries and have limited resources in terms of memory and computational power. It signifies that specific lightweight and energy-efficient algorithms are required to be implemented for the devices. Researchers all around the world are now developing solutions to tackle the challenges of IoT devices due to quantum computing.
Back in October 2019, the search engine giant Google proclaimed to have achieved quantum computing because its 54 qubit SoC had the ability to perform a calculation in just 200 seconds that would have surpassed a powerful supercomputer. The coming years, once this type of chips are commercialized, cybercriminals could easily crack any security encryptions. Now, the point is what could be the possible security solutions. The Quantum Random Number Generator (QRNG) refers to quantum driven secure chip design, which can be integrated into current Silicon design and manufacturing processes. Another option is to choose a configuration with as much memory as possible. It is forecasted that implementing at least 256kb of RAM for cryptography within the Root of Trust will be secure enough for the post-quantum world. Now, unlike asymmetric encryption, symmetric encryption does not require keys to be sent in the open, where quantum algorithms could potentially break it. Instead, it requires that the sender and recipient of a message exchange an encryption key in person. Implementation of Symmetric crypto accelerators will play a key role for post-quantum crypto algorithms.






I i am Sam Colley is an expert in telecoms and CEO of Pod Group. I read your blog and I Think For IoT gadgets to function properly, they will require secure hardware, software, and communication. Any connected equipment, from refrigerators to factory robotics, can be hacked if IoT security isn't in place. Hackers can takeover the object's functioning and steal the user's digital data once they gain control.